This Item Ships For Free!
Trojan horse attack top
Trojan horse attack top, Trojan Horse Attack In Cyber Security by Adel the whiteboard top
4.91
Trojan horse attack top
Best useBest Use Learn More
All AroundAll Around
Max CushionMax Cushion
SurfaceSurface Learn More
Roads & PavementRoads & Pavement
StabilityStability Learn More
Neutral
Stable
CushioningCushioning Learn More
Barefoot
Minimal
Low
Medium
High
Maximal
Product Details:
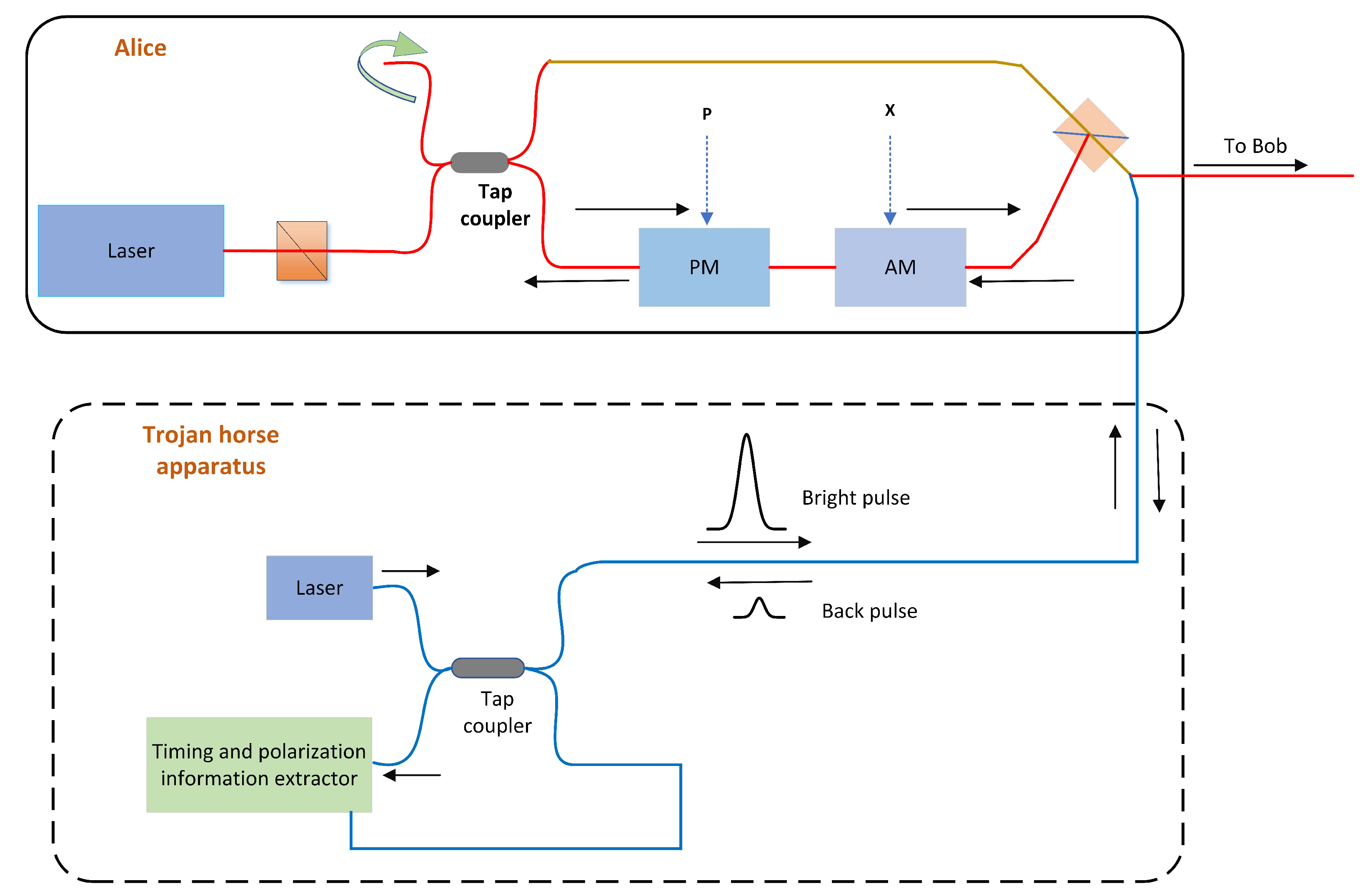
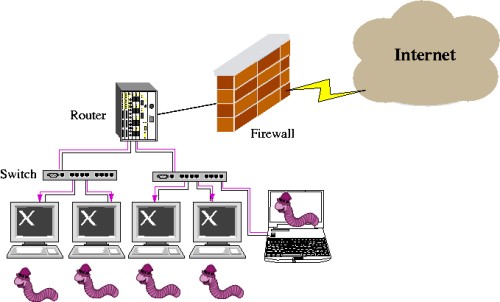
Trojan horse virus mal ware cyber security attack Vector Image top, Trojan attack PPT top, What is a Trojan Horse U.S. News top, What Is a Trojan Virus Definition Types Prevention Tips top, Trojan Horse Virus History Types and Working top, Trojan horse attacks threaten the security of practical quantum top, CCNA Security Worm Virus and Trojan Horse Attacks top, Applied Sciences Free Full Text Practical Security Bounds top, What Is a Trojan Horse in Computer Terms InfoSec Insights top, Trojan Horse Attack In Cyber Security by Adel the whiteboard top, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet top, Principle of a Trojan Horse attack. Eve occupied part of the top, The working principle of Trojan horse attack. Reprinted from Ref top, Risk analysis of Trojan horse attacks on practical quantum key top, Trojan horse PPT top, What are Banking Trojans GeeksforGeeks top, What is a Trojan horse attack Shiksha Online top, What is a Trojan Horse Virus Attack Littlefish Guide top, Preview The Real Trojan Horse top, How the attacker used the Trojan horse to attack Download top, Trojan Virus Vector Symbol With Laptop And Red Trojan Horse Stock top, Trojan Horse Meaning Examples Prevention top, 7 Phases of a Trojan Horse Attack Edafio top, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus top, What is a Trojan Horse Virus Types and How to Remove it top, Trojan horse attacks threaten the security of practical quantum top, What Is a Trojan a Virus or Malware How Does It Work Avast top, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses top, 7 Phases Of A Trojan Horse Attack top, Trojan Attacks How Does Trojan Horse Infect Devices top, Scheme of a Trojan horse attacks with different wavelengths from top, What is a Trojan horse attack Shiksha Online top, What is a Trojan Horse Virus Types Prevention in 2024 top, What is a Trojan Horse Virus Types Prevention in 2024 top, What is a Trojan Virus Trojan Horse Malware Imperva top, Product Info: Trojan horse attack top.
- Increased inherent stability
- Smooth transitions
- All day comfort
Model Number: SKU#6991915